SQL Injection
What is SQL Injection?
A SQL Injection attacks consists of insertion or "injection" of a SQL query via the input data from the client to the application.
How SQL Injection attacks?
=>SQL injection is frequently used to bypass authentication mechanisms.Attackers can gain access to other information systems and can access other user details.
=>Read unauthorized information from the database.
=>Grab username and password from user defined table.
=>Modify database data like Insert/Update/data.
=>Execute administration operations on the database.
=>Recover the content of a given file present on the DBMS file system.
=>Issue commands to the operating system.
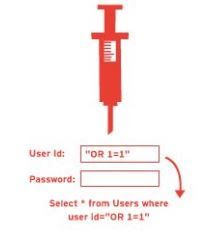
Consider below this SQL query for authenticating a user to a web application.
Suppose the hacker enters the username as OR 1=1-- the SQL query becomes
Because the double hyphens character is interpreted as the beginning of a comment by the SQL server everything after'--'is
Since 1-1 is always true the authentication mechanism will be bypassed and the application will let the hacker in
How to prevent SQL Injection:
=>Use stored procedures for interacting with database
=>Call stored procedures through a parameterized API
=>Validate all input through generic routines
=>Use the principle of "least privilege"
=>Define several roles,one for each kind of query
A SQL Injection attacks consists of insertion or "injection" of a SQL query via the input data from the client to the application.
How SQL Injection attacks?
=>SQL injection is frequently used to bypass authentication mechanisms.Attackers can gain access to other information systems and can access other user details.
=>Read unauthorized information from the database.
=>Grab username and password from user defined table.
=>Modify database data like Insert/Update/data.
=>Execute administration operations on the database.
=>Recover the content of a given file present on the DBMS file system.
=>Issue commands to the operating system.
Consider below this SQL query for authenticating a user to a web application.
SELECT * FROM users WHERE username ='navas' AND password ='123'
Suppose the hacker enters the username as OR 1=1-- the SQL query becomes
Because the double hyphens character is interpreted as the beginning of a comment by the SQL server everything after'--'is
Since 1-1 is always true the authentication mechanism will be bypassed and the application will let the hacker in
How to prevent SQL Injection:
=>Use stored procedures for interacting with database
=>Call stored procedures through a parameterized API
=>Validate all input through generic routines
=>Use the principle of "least privilege"
=>Define several roles,one for each kind of query







No comments: